Creating a digital certificate store
The KeyTool command-line program enables you to create a Rational® Certificate Store (RCS) file that contains digital certificates for use with tests. A Rational® Certificate Store (RCS) file is a compressed archive file that contains one or more PKCS#12 certificates. You can also use the KeyTool program to remove certificates from a certificate store.
About this task
Rational® Performance Tester acts as a proxy between the browser and the server application to record the data exchange. When a secured page is recorded using Rational® Performance Tester, the proxy certificate of the product is presented to the browser.
Procedure
- In the command line tool, navigate to the directory that contains the Keytool utility. By default, the utility is located at C:\Program Files\IBM\SDP\jdk\jre\bin.
-
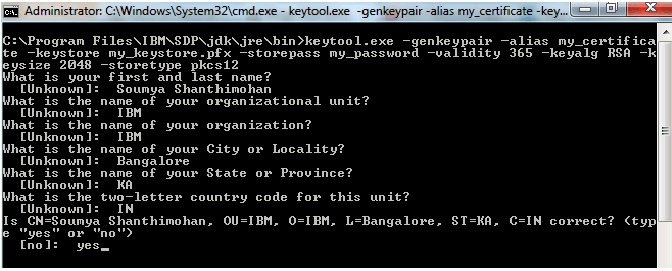
Type the following command:
keytool.exe -genkeypair -alias certificateName -keystore keystoreName -storepass password -validity 365 -keyalg RSA -keysize 2048 -storetype pkcs12
For additional information about parameters by certificate generation, review the official keytool documentation.
Option Description -genkeypair Generate public and private keys for key pair. -alias Alias for your certificate in the key store. You may never use it, but every new certificate in your key store must have its own alias. -keystore Name of the key store file, which will be generated as the result of the command. It holds your certificate and a corresponding private key. You can reuse this key store for next certificates that you might generate. One key store can contain many certificates. -storepass Password that protects your key store file. You will have to enter it every time you want to sign a document.
-validity Number of days the certificate is valid. You can enter more than 365. -keyalg Algorithm to generate the cryptographic keys that is corresponding to your certificate. You can use RSA or DSA. -keysize Length of the cryptographic keys. The more the length the stronger the signature. -storetype Format of the key store file. PKCS#12 (a.k.a PFX) key stores can be understood by a lot of different programs and you can also import a PKCS#12 file in your Windows key store (just double click it and follow the instructions). -
The certificate generation process prompts you to enter some information about you. Enter the
information as prompted.
-
If prompted for a password when using the keystore, enter the same password as provided on the
command line.
The key store file (.pfx) is stored in your current directory.
Results
You now have a digital certificate store that you can use with tests. Because the KeyTool program has many options, you might want to create an alias or script file to use to invoke KeyTool. Use KeyTool to create and add as many digital certificates as you want. If you want to create a dataset of the names of certificates in the certificate store, run KeyTool again with the -list option. This option writes a list of names that can then be imported to a dataset.
What to do next
You do not have to use the KeyTool command-line program to create a certificate store. It is possible to use existing PKCS#12 certificates with Rational® Performance Tester. PKCS#12 certificates can be exported from a web browser. PKCS#12 certificates encode the private key within the certificate by means of a password.